Running sFlow-RT with Traffic Sentinel
This tutorial describes the steps to run the real-time analytics platform sFlow-RT on a server that is already running Traffic Sentinel.
1. Install sFlow-RT package
Install sFlow-RT from rpm or debian package so that it appears under /usr/local/sflow-rt/
sudo yum install sflow-rt-3.1-1714.noarch.rpm sudo systemctl enable sflow-rt
2. Configure sFlow-RT
In /usr/local/sflow-rt/conf.d/sflow-rt.conf, uncomment the setting for sflow.port and set it to 6344, and uncomment the setting for http.hostname.
# listen for sFlow on UDP port 6344 sflow.port=6344 # only accept connections from localhost http.hostname=127.0.0.1
Install one or more of the sFlow-RT apps:
sudo /usr/local/sflow-rt/get-app.sh sflow-rt browse-metrics sudo /usr/local/sflow-rt/get-app.sh sflow-rt browse-flows
3. Start sFlow-RT
sudo systemctl restart sflow-rt
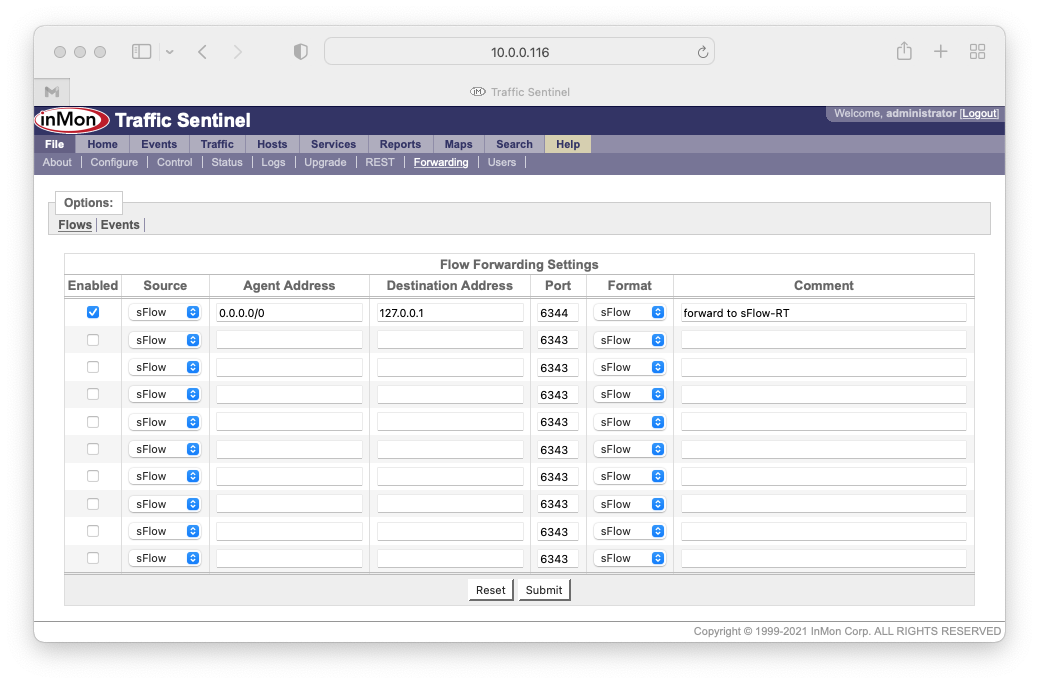
4. Forward sFlow from Traffic Sentinel
In the Sentinel UI under File>Forwarding>Flows, enable an entry to send sFlow from agent=0.0.0.0/0 (all agents) to 127.0.0.1 on port 6344.
5. Add sFlow-RT Apache config
Starting with the example on the sFlow-RT downloads page, add the apache config to reverse-proxy everything under /sflow-rt/ to sFlow-RT, and add access-control policy there. For example if only clients in 10.10.100.0/24 should see sFlow-RT then this goes in /etc/httpd/conf.d/sflow-rt.conf.
<IfModule mod_proxy.c>
ProxyRequests off
ProxyVia off
ProxyPass /sflow-rt/ http://127.0.0.1:8008/ retry=0 timeout=5
ProxyPassReverse /sflow-rt/ http://127.0.0.1:8008/
<IfModule mod_headers.c>
RequestHeader append X-Forwarded-Prefix "/sflow-rt/"
</IfModule>
</IfModule>
<Location /sflow-rt/>
<RequireAny>
Require ip 10.10.100.0/24
</RequireAny>
</Location>
6. Reload Apache
sudo systemctl reload httpd
You should now be able to access sFlow-RT under the /sflow-rt/ URL (while Traffic Sentinel is still under the /inmsf/ URL). By default when you connect to the server you are redirected to /inmsf/.

See Getting Started for more information on sFlow-RT.
